A vulnerability refers to weaknesses or flaws in an IT network that attackers can exploit to gain unauthorized access, perform malicious actions, or compromise the security of an organization’s data and network. Cybercriminals are constantly on the lookout for vulnerabilities to exploit, using them as a means to launch attacks such as data breaches, malware infections, or denial of service attacks. This is where Pen testing services come into play, identifying and addressing these weaknesses before they become a real threat.
Vulnerability Management
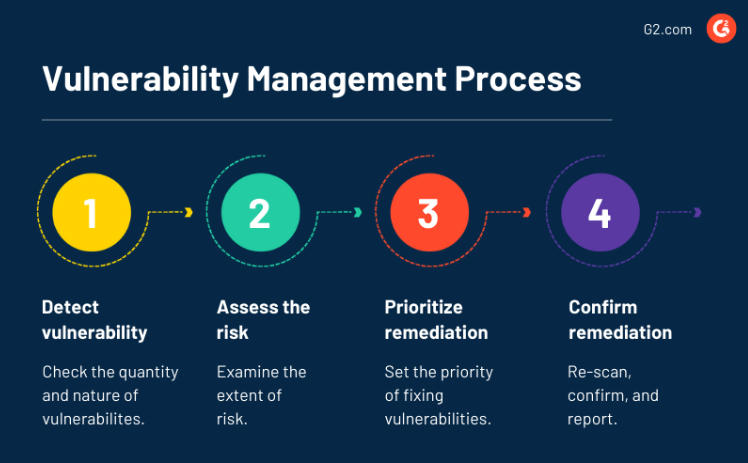
Implementing a robust vulnerability management strategy is crucial for identifying, evaluating, and addressing these weaknesses before they can be exploited by malicious actors. This ongoing process includes regular VAPT testing and vulnerability assessments to discover potential threats and mitigate risks effectively.
The Importance of a Vulnerability Management System
A comprehensive vulnerability management system is essential for maintaining the security of an organization’s IT infrastructure. Vulnerability management systems provide automated tools to detect and remediate vulnerabilities, ensuring that the network remains secure against potential threats. Integrating Pen testing services and VAPT testing into your vulnerability management strategy enhances your ability to detect and address these issues proactively.