In cybersecurity, a threat is any potential event or action that exploits vulnerabilities to harm an organization’s digital assets or reputation. Cyber threats can take many forms, such as:
YOUR IT INFRASTRUCTURE NEEDS A PROACTIVE PROTECTION
What is a Threat?
Malware
Malicious software causing system damage
Phishing
Deceptive tactics to obtain sensitive information
Denial-of-service (DoS) attacks
Overwhelming systems with excessive traffic
Insider threats
Compromises by employees or partners with access to sensitive data
Advanced persistent threats (APTs)
Sophisticated, long-term attacks targeting high-value organizations.
What causes it
Understanding the root causes of cyber threats is crucial for your business to develop an effective defence strategy. Threats arise from multiple sources, such as:
Cybercriminals
Hacktivists
Nation-state actors
Insider threats
Software vulnerabilities
Human error
Outdated systems
By identifying these causes, organizations can establish a comprehensive cybersecurity plan that minimizes risks and safeguards their digital assets.
What happens when you neglect it?
Neglecting to address a threat in cybersecurity can have severe consequences for your organization, such as:
Data breaches
Financial losses
Disruption of operations
Reputation damage
Legal and regulatory penalties
Increased vulnerability
To minimize these risks, organizations should adopt a proactive approach to cybersecurity, regularly assess their security posture, and promptly address threats to protect their digital assets and maintain business continuity.
Stay ahead of threats with Pathway
At Pathway, we take a comprehensive approach to threat management, ensuring that your organization is protected from evolving cyber threats. Our cybersecurity experts work tirelessly around the clock to keep your organization safe from cyber threats. We’re dedicated to delivering proactive, comprehensive, and tailored solutions that protect your valuable IT assets from attacks.
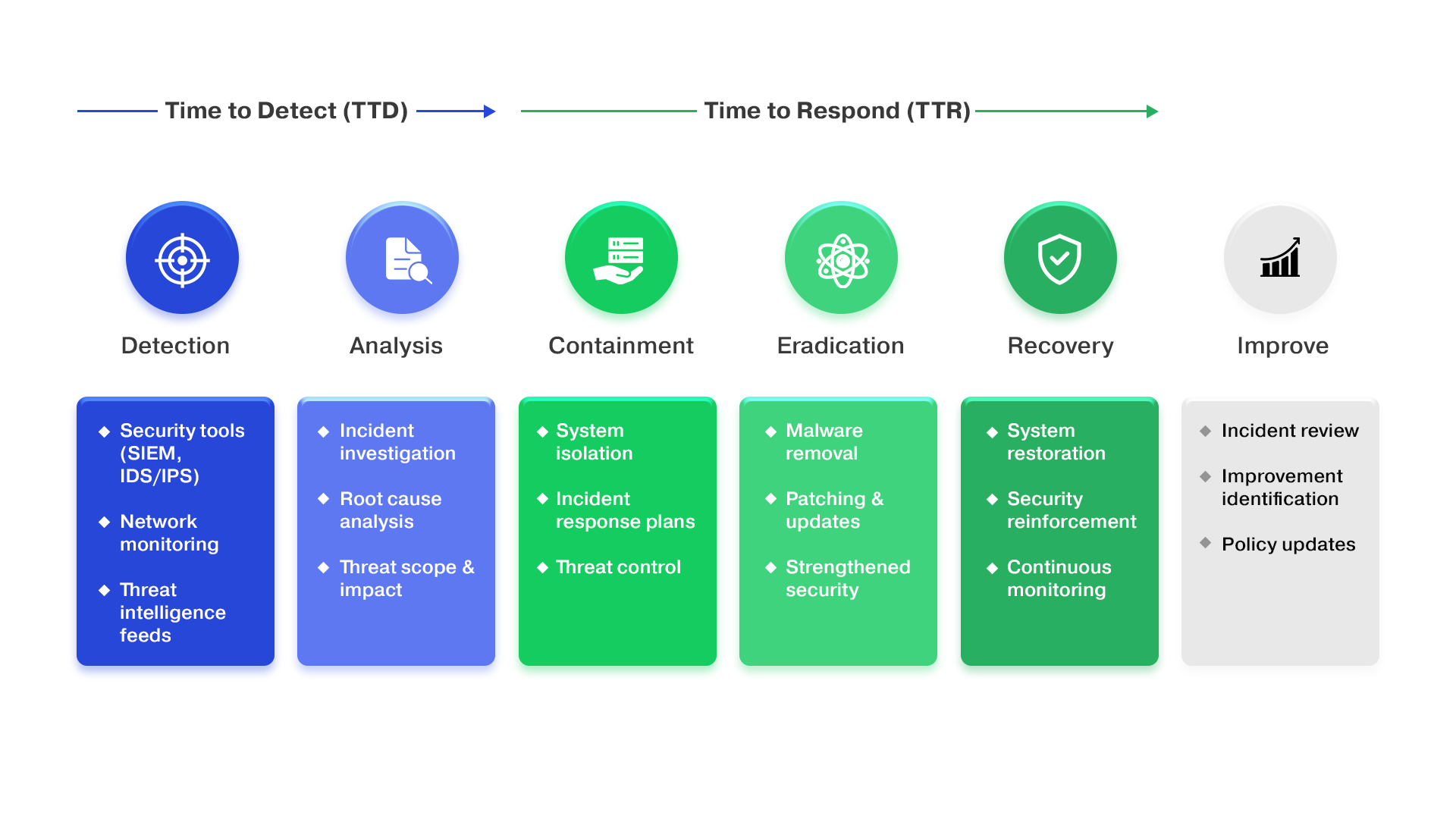
What we offer
Pathway’s Threat Management framework leverages the combined power of Threat Intelligence and Threat Hunting, offering a comprehensive and proactive defence strategy customized to meet your organization’s specific requirements.
| Threat Intelligence | Threat Hunting | |
| Focus | Collects, analyze, and disseminate information about existing and emerging threats. | Proactively search for potential threats, signs of compromise, or suspicious activities within an IT environment. |
| Result | Indicators of Compromise (IoCs), threat actor profiles, and vulnerability information. | Detection of anomalous behaviors, compromised systems, and evidence of intrusion. |
| Value | Improved situational awareness, proactive defense measures, and informed security decisions. | Early detection of threats, reduced dwell time, and increased overall security posture. |
| Scope | External threats | Internal threats |
| Approach | Reactive | Proactive |
| Tools & Techniques | Security Information and Event Management (SIEM), threat intelligence platforms, and analytics tools. | Endpoint Detection and Response (EDR), User and Entity Behavior Analytics (UEBA), and network traffic analysis. |
| Data sources | Open-source intelligence (OSINT), commercial feeds, industry forums, government alerts, and dark web. | Network logs, endpoint data, security event data, and user behaviour analysis. |
By choosing Pathway for your threat management needs, you can be confident in the knowledge that our team of cybersecurity experts is working tirelessly to keep your organization safe from cyber threats. We’re dedicated to delivering proactive, comprehensive, and tailored solutions that protect your valuable assets from attacks.
Perks of Threat Management
Our technology partners for advanced cybersecurity
Pathway uses a variety of vetted commercial software platforms and tools to deliver the best security services.


Microsoft

Tenable

FortiNet

Rapid7

Kaseya

Elastic Software

RapidFire

Zabbix

KnowBe4

BitDefender

Duo

ESET

Ridge Security

Sprinto
Why choose us?
Fully-equipped, world-class security operations center
Pathway Communications operates a world-class Security Operations Center (SOC) in Markham with experienced security professionals dedicated to protecting your business. Our SOC is equipped with state-of-the-art technology, advanced threat detection and response tools, and a team of elite analysts working 24/7 to monitor your systems and respond to potential threats.
24/7 vigilance against threats
Threats can emerge at any time, day or night. That’s why Pathway offers round-the-clock Managed Detection and Response (MDR), which combines continuous monitoring of all assets, accurate alerts, detection, and rapid response to cyber security events. This ensures your IT infrastructure and applications are properly configured, hardened, and protected with the help of our world-class Security Operations Centre (SOC), which monitors, detects, and responds 24/7.
SMB-friendly
Cybersecurity is essential for a business, and Pathway Communications believes in making this essential service accessible for businesses of all sizes. That’s why we offer tailored security solutions that fit the needs and budgets of mid-sized and smaller organizations.
24/7 access to SOC Cyber Analysts and Elite Threat Hunters
Pathway offers 24/7 access to our team of SOC Cyber Analysts and Elite Threat Hunters so that you can turn to us for help with any cybersecurity issue at any time. This helps to reduce the impact of cyber incidents and minimize downtime, ultimately saving you time and money. Additionally, the peace of mind that comes with knowing that expert support is always available can help you to feel more secure and confident in your cybersecurity posture.
Easy access to reports and records
Pathway’s security systems store your data for reporting and analysis and provide you with access to reports, cases, dashboards, and event updates via a web portal or scheduled batches. You can easily view and analyze your data offline to make informed decisions about your cybersecurity.
Customization
Pathway offers a complete range of security services with budgets of any size. These include packages of bundled services or individual (“a-la-carte”) services which cater to the specific needs of our clients.
Certified experts
Pathway’s team of experienced professionals has expertise in cybersecurity, including risk management, threat analysis, incident response, and compliance. They have a wide range of skills and technical certifications for proactive monitoring and support to your business.
- Certified Information Systems Security Professional (CISSP)
- Certified Cloud Security Professional (CCSP)
- Certified Information Systems Auditor (CISA)
- Cisco Certified Internet Engineer (CCIE) – security and routing
- Unix System Administrators
- Microsoft Certified Solutions Expert (MCSE)
- Microsoft Certified: Azure Solutions Architect (MCASA)

